Task 4, is the first time that requires interaction with the blockchain.
[references for interacting with smart contracts]
We are tasked with determining all the victims for an Escrow contract and which ones have actually paid the ransom. There are multiple methods for determining this information, depending on if we want to analyze the Escrow or Register contracts and look at the contract storage or events generated by the contracts.
Below are the variables tracked by the Escrow contract:
address owner; //!< This is the account that deployed the Escrow contract
uint ownerBalance; //!< This is the account balance of the owner (i.e., fulfilled ransoms)
address registry; //!< This is the address of the Registry contract
mapping(uint => address) vicToPayerMap; //!< Mapping from victim IDs to the account addresses that submitted payment
mapping(uint => Victim) victimMap; //!< Mapping from victim IDs to Victim structs
mapping(uint => bytes32) decKeyMap; //!< Mapping from victim IDS to decrypted ransom keys
mapping(address => uint) ransomMap; //!< Mapping from Ransom contract addresses to victim IDs
mapping(uint => uint) escrowMap; //!< Mapping from victim IDs to the amount of ransom payment received
mapping(uint => string) encFileMap; //!< Mapping from victim IDs to encrypted test files
address[] ransomContracts; //!< List of Ransom contracts registered with this Escrow contract
address oracleAccount; //!< Address of the off-chain authentication and decryption Oracle
A contracts storage can be examined using python Web3’s function <>.
# read variable in storage
w3.eth.getStorageAt('0x5449F8636F1886675cc6b3F491dD27b5A861fba7', 0)
# read array in storage, hash(<variable spot>)
hash = web3.Web3.soliditySha3(['uint256'], [9])
w3.eth.getStorageAt('0x5449F8636F1886675cc6b3F491dD27b5A861fba7', hash.hex()) # first element
w3.eth.getStorageAt('0x5449F8636F1886675cc6b3F491dD27b5A861fba7', hex(int(hash.hex(), 16) + 1)) # second element
# read mapping in storage, hash(<variable spot>, <vid>)
hash = web3.Web3.soliditySha3(['uint256', 'uint256'], [4, 0x23ece81486ba240261ecd43dc05abfe4b2fc2e9767554852b9131b8f45f83dd6])
w3.eth.getStorageAt('0x5449F8636F1886675cc6b3F491dD27b5A861fba7', hash.hex())Code to get all contracts registered with Escrow
hash = web3.Web3.soliditySha3(['uint256'], [9])
contracts = []
for i in range(0, 0xd):
contracts.append(w3.eth.getStorageAt('0x5449F8636F1886675cc6b3F491dD27b5A861fba7', hex(int(hash.hex(), 16) + i)))[contracts]
After we have the list of contracts, they can be checked to determine which victims have paid the ransom.
This can be done by ransomContract->ransomMap->(decKeyMap or vicToPayerMap)
[checking map]
or we can check Events using
ev_filter = escrow.eventFilter('DecryptEvent', {'fromBlock' : 0, 'toBlock' : 'latest'})
events = ev_filter.get_all_entries()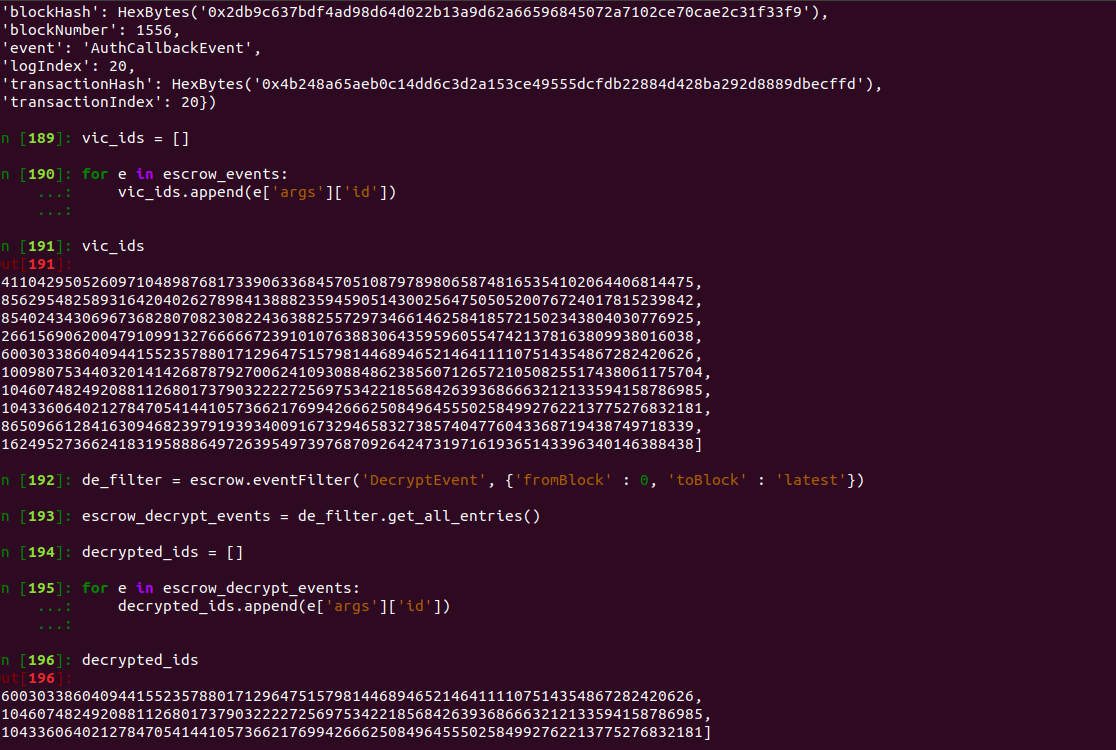
Victims that have not paid:
- 0x5ae034e049c13cfdaf9bc2497221812f90af61e6fcee5d0c3c583dd364275f0b
- 0xbd509b56d37e518c69fc74049e543e921f152e5cf41e47ed42d07bf0acfe3ca2
- 0xbcd0109a269c03d7ac11c45f3771d3e060e3e8252b69862293974194c4a3765d
- 0x3ad7f27186d93b62015fa459a505f2a97aca3e082ee3f71407fc243592978726
- 0xdf4114bd9e6d40a0ae0d9ecd5601b994c54819890f327889ef5bbf9726aee398
- 0xbf42bbad4a81196088b30963162b5f42714ccbe833c0a024fc6810f32f415743
- 0x23ece81486ba240261ecd43dc05abfe4b2fc2e9767554852b9131b8f45f83dd6
Victims that have paid:
- 0x84b7f7b3c8140714fb37f4b74cc50b54d222aaee62c217952ba8d9d9c708a392
- 0xe745bca6ad01364a09a80ee79ad890c9557147badd29e26f0264af2a927ee9a9
- 0xe6ac1e980ffb332763186ed852d095c3a8f59d52ac6c37b9f514253e74c8f5b5
