Task 2 requires you to examine the android app TerrorTime to extract basic metadata. To complete this task you need to submit
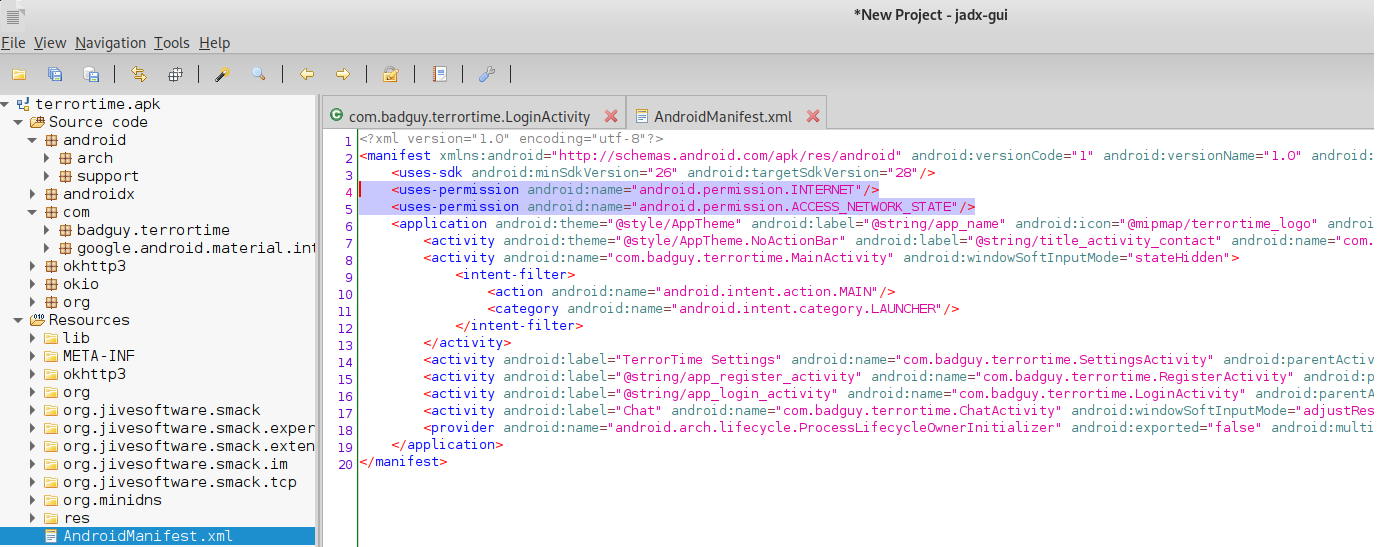
- the APK’s permissions,
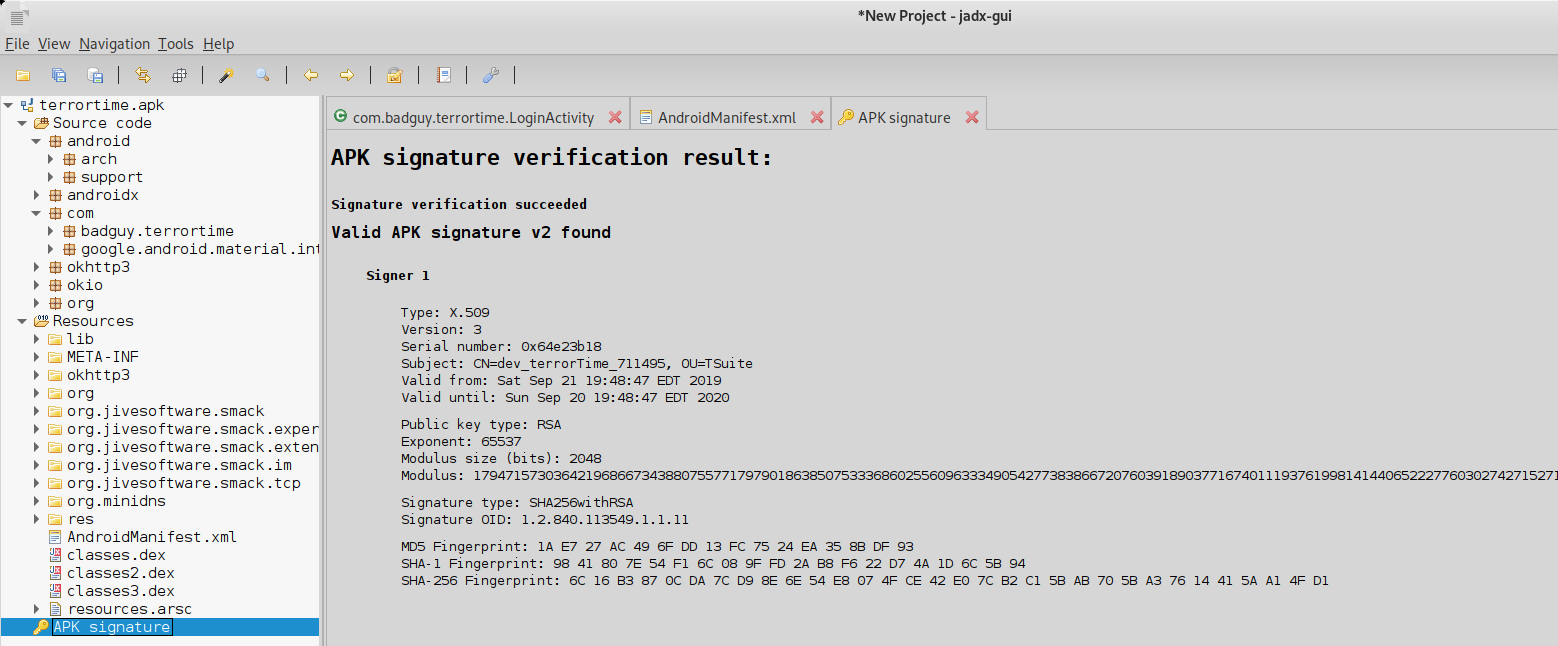
- the SHA256 of the code signing certificate, and
- the common name of the certificate signer.
I used the tool jadx to read TerrorTime’s AndroidManifest.xml file to determine the permissions.
It took me some time to extract the signing certificate. A Google search will provide instructions to extract the certificate using tools such as unzip, jarsigner or apktool. These methods are for APK Signature Scheme v1 which is based on signed JAR. TerrorTime was signed using APK Signature Scheme v2 which inserts the certificate into the ZIP file before the central directory. This enables verification of the ZIP contents and metadata.
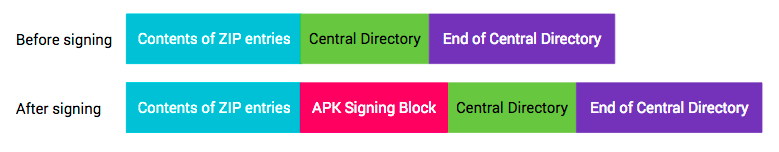 Image from Android Source
Image from Android Source
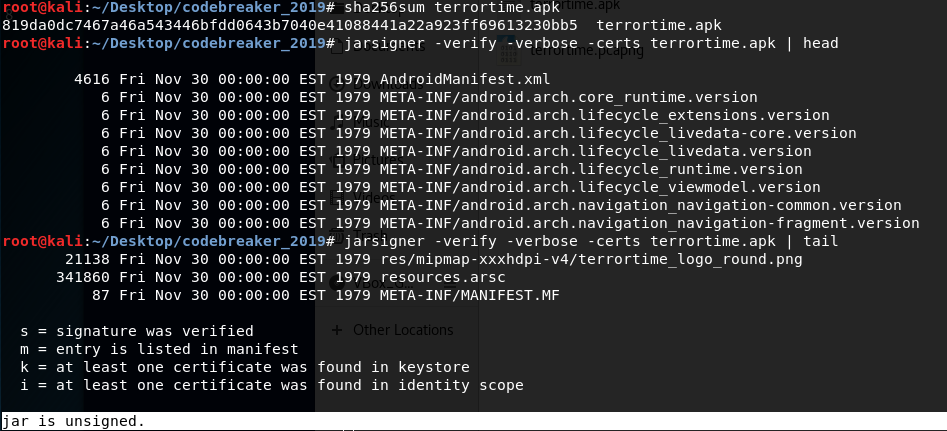
If the APK is decompressed using a tool like unzip, the certificate data is ignored and it appears as if the app was not signed. Below is the output of jarsigner.
The tool jadx can extract and parse the APK Signature Scheme v2 certificate. The common name is listed under subject as CN. The common name for the certificate is dev_terrorTime_711495. The SHA256 is at the bottom under SHA-256 Fingerprint.