Task 3 requires you to examine the TerrorTime’s local database. To complete this task you need to submit
- IP address of the OAUTH server and
- IP address of the XMPP server.
I was provided a SQLite database that was recovered from a device with TerrorTime installed. I used DB Browser for SQLite to open and examine the database.
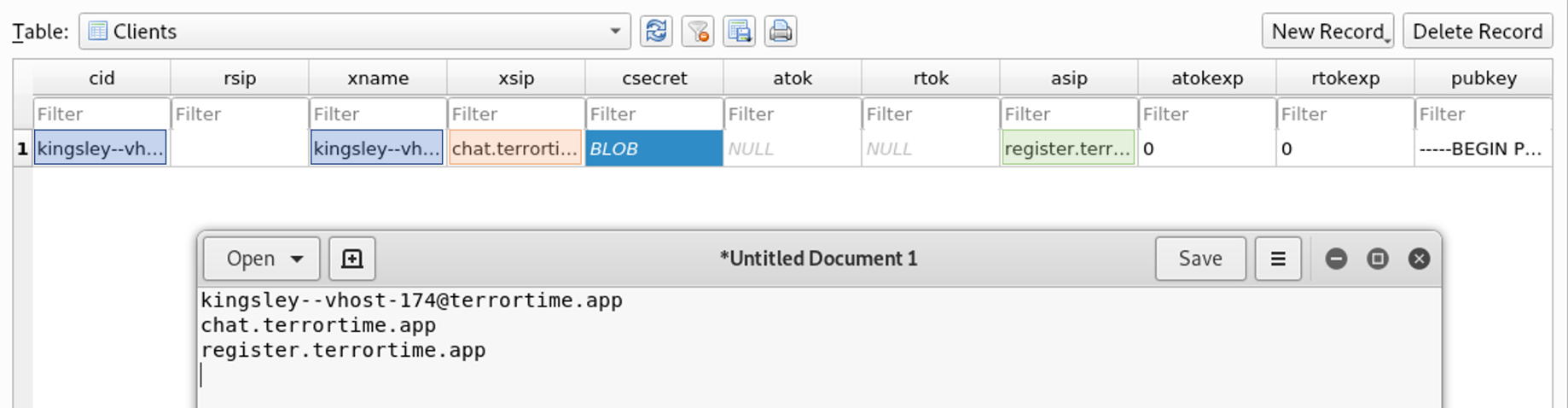
I found two fully qualified domain names (FQDNs). The hostnames indicate they are for registration and chatting. I checked TerrorTime’s decompiled code in jadx to verify my interpretation. TerrorTime contains a class called ClientDBHandlerClass that handles interacting with the client’s database.
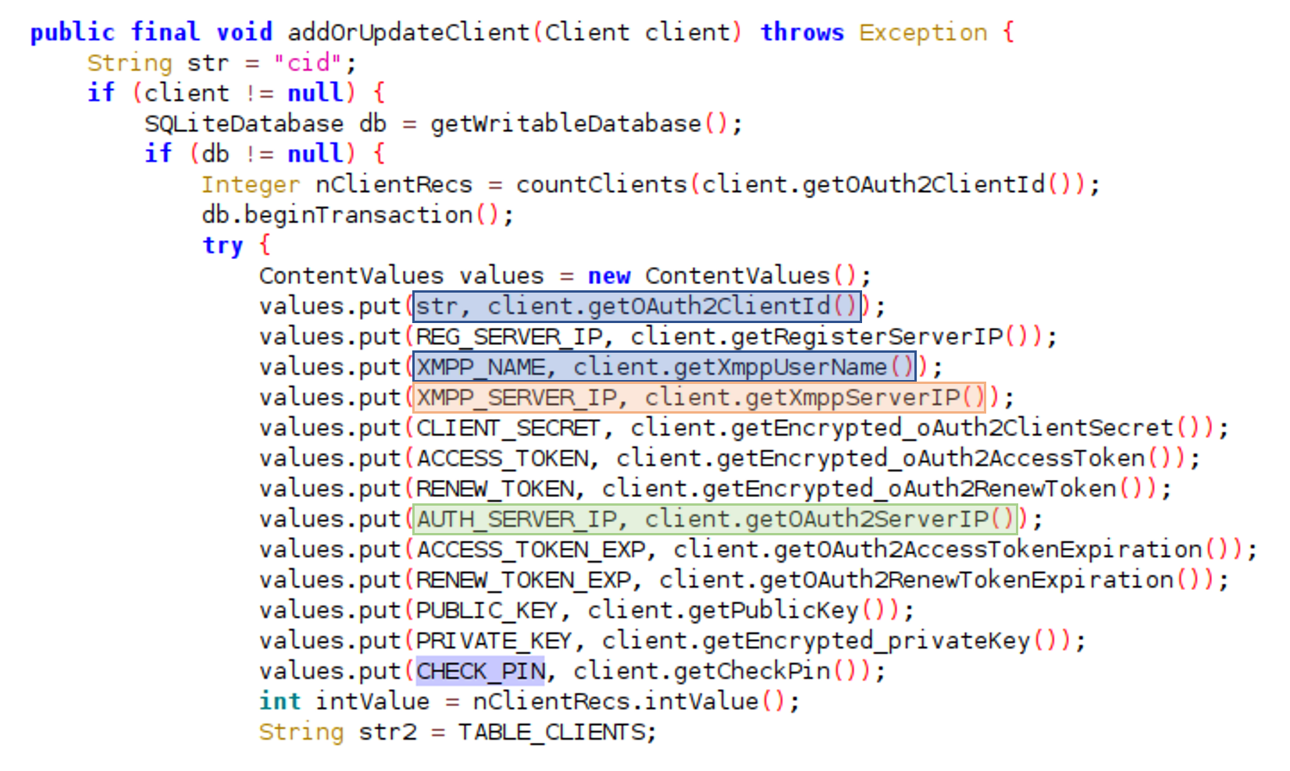
I found the below information by analyzing the variable names in the ClientDBHandlerClass.addOrUpdateClient function. One thing to note for later is that the username appears twice; in column one and column three.
Below is a brief explanation of the different columns.
- Col 1 - ClientID for OAuth
- Col 2 - Server IP for registration
- Col 3 - User’s XMPP name
- Col 4 - XMPP Server IP
- Col 5 - Client secret (used for OAuth and encrypting)
- Col 6 - Access Token (Used for accessing XMPP Server)
- Col 7 - OAuth Renew Token
- Col 8 - Access Token expiration
- Col 9 - Renew Token expiration
- Col 10 - RSA Public Key
- Col 11 - Encrypted RSA Private Key
- Col 12 - Encrypted pin for accessing TerrorTime application
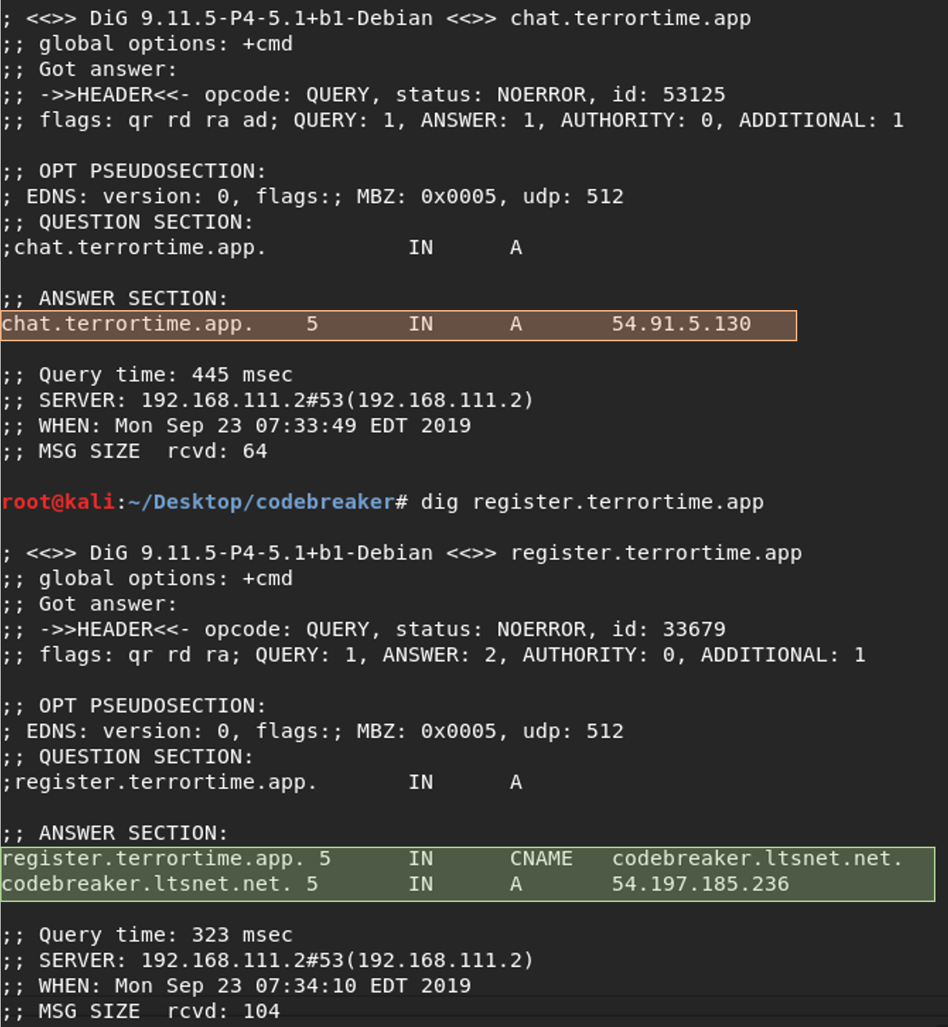
The command dig can resolve a domain name to an IP address.
- chat[.]terrortime[.]app resolves to 54[.]91[.]5[.]130
- register[.]terrortime[.]app points to codebreaker[.]ltsnet[.]net which resolves to 54[.]197[.]185[.]236